CNAS Releases Amy Chang’s Report on China’s Cyber Strategy
Click here to read Amy Chang’s interview in New York Times.
Download full text of the report here.
CNAS Releases Report on China’s Cyber Strategy
Report Reveals the Political, Economic, and Military Objectives
of China’s Cybersecurity Strategy
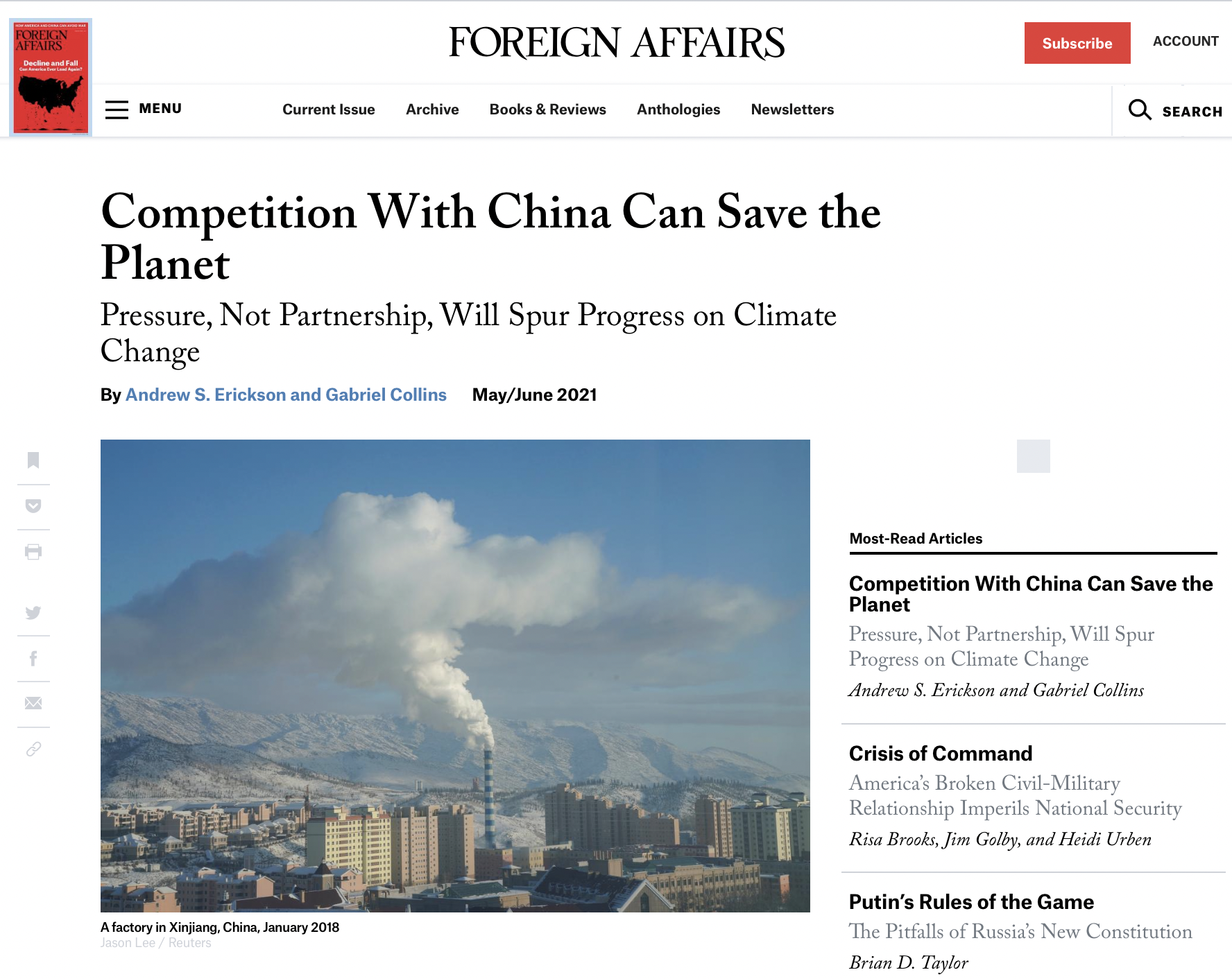
Washington, December 3 – Center for a New American Security (CNAS) Technology and National Security Program Research Associate Amy Chang has written a new report, “Warring State: China’s Cybersecurity Strategy.” The report explores the political, economic, and military objectives of China’s cybersecurity apparatus; reveals drivers and intentions of Chinese activity in cyberspace; and analyzes the development of Beijing’s cybersecurity infrastructure over the last three decades.
Please find an executive summary of the report by Ms. Chang below:
The United States-China cyber relationship has rarely been more fraught than it is today. Despite high levels of attention to cybersecurity issues in both countries over the past several years, the two nations continue to face substantial obstacles in developing cooperative efforts and improving mutual understanding on the issue. In the cyber context, relations have devolved to near-complete distrust of each other’s motives, actions, and agendas, affecting other facets of the bilateral relationship.
What can be done to improve this situation?
Devising an optimal strategy to address the challenges in the U.S.-China cyber relationship first requires an understanding of motives, agendas, and stakeholders embedded in the process. In this light, this report uses interdisciplinary methods and analysis and Chinese language research to provide unique insight on China’s cybersecurity strategy, including its development since the 1990s, its infrastructure and influencers, and its objectives and incentives in the cyber realm – especially as it pertains to China’s foreign policy and its interactions with the United States.
China’s foreign policy behavior, including its cyber activity, is driven primarily by the domestic political imperative to protect the longevity of the Chinese Communist Party. Ensuring domestic stability, territorial integrity, modernization, and economic growth, while simultaneously preparing for the possibility of militarized cyber conflict in the future, are all objectives that directly or indirectly support the continuation of CCP rule. China espouses laws, norms, standards, and agreements in bi- and multilateral fora that allow for sufficient flexibility of interpretation to serve domestic needs and interests.
Senior CCP officials have also issued high-level directives and created several high-level Leading Groups and Leading Small Groups to provide strategic guidance on cybersecurity. Concurrently, there has been a noticeable increase in civilian and military research and development on cybersecurity strategy and defensive and offensive cyber tools over the past several years.
Beijing’s thinking about cybersecurity, and its cybersecurity strategy consists of three main component drivers: economic, political, and military. Important manifestations of those drivers are:
- Maintaining economic growth and stability, which involves industrial economic cyber espionage of U.S. and other foreign targets
- Protecting the governing power of the Chinese Communist Party through information control, propaganda, and targeting of domestic sources of potential unrest
- Using computer network operations to signal dissatisfaction with foreign powers over developments outside of China (e.g., maritime territorial disputes, foreign allegations of Chinese hacking activity) that negatively affect China’s reputation
- Preparing for military scenarios and ensuring military superiority in the event of cybered conflict with an adversary through military modernization, computer network operations research, and human capital cultivation
- Studying and understanding potential adversaries’ military infrastructures, motivations, objectives, capabilities, and limitations in the cyber domain
- Advancing alternative narratives of government control over/handling of cybersecurity internationally (e.g., promoting sovereignty of states to control the Internet within a country’s borders) and domestically (e.g., justifying domestic surveillance, information control)
Domestic policy and military developments over the past several years indicate that cybersecurity is a high priority for the Chinese government. Despite high-level guidance and strategic direction from Xi Jinping and senior civilian and military officials, implementation of China’s cybersecurity strategy remains fragmented and its bureaucratic structure remains disorganized, characterized by competition for stakeholder resources and influence on policy direction.
Chinese behavior will not change in the foreseeable future, unless major shifts in politics (e.g., changes in U.S. approaches to engagement/conflict with China) or incentives change China’s domestic and foreign policy risk calculus and objectives. To achieve this, the United States must understand China’s perspectives and goals and distinguish areas of common interest and contention, and craft an appropriate strategy that provides incentives and shapes China’s behavior. Such a strategy cannot be contained purely in the cyber context, and must be iterative and collaborative across U.S. public and private sectors.
This report contributes a solid foundation of understanding of China’s cybersecurity strategy, and aims to inform U.S. efforts in negotiating with China on cyber issues. As such, this report hopes to illuminate, though it is not a solution in itself. Any solution must leverage U.S. advantages in this realm and increase China’s risk calculus sufficiently to alter China’s behavior. A follow-on policy brief providing recommendations for addressing the U.S.-China cyber relationship will be released in early 2015.
Ms. Chang is available for interviews on this report. To arrange an interview, please contact Neal Urwitz at nurwitz@cnas.org or call 202-457-9409.